Revamping Your Crypto Marketing Strategy for Success
Promoting a cryptocurrency project may seem intimidating at first. This is understandable, especially as it is based on a relatively new technology that few people understand and requires putting their capital at risk.
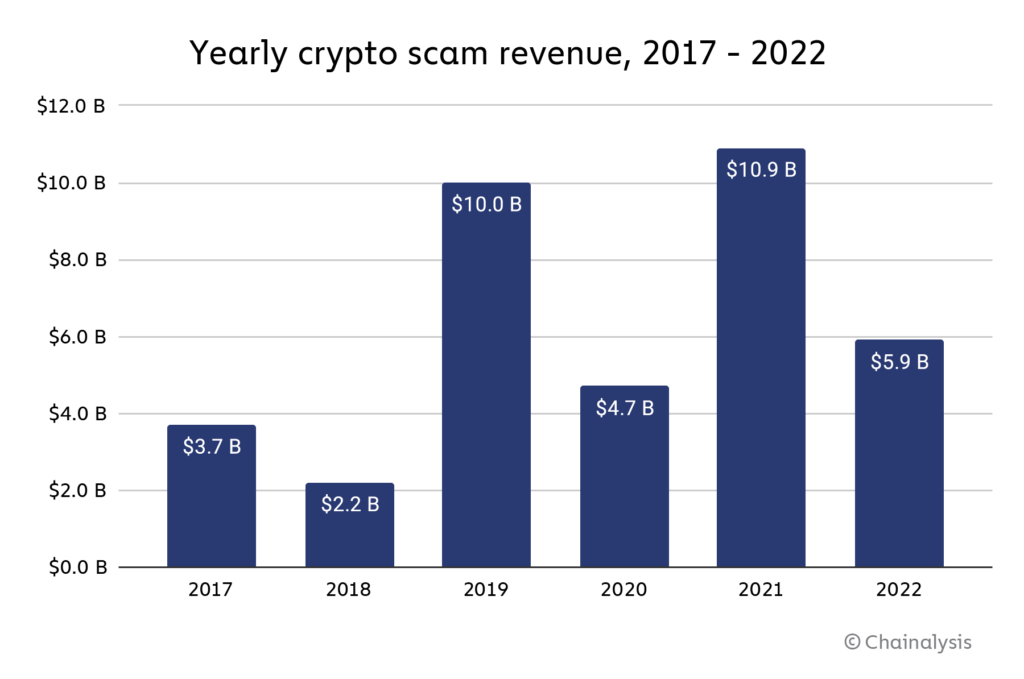
Moreover, the prevalence of scams in the market doesn’t instill much confidence; in 2022 alone, $5.9 billion was lost to crypto scams, a 46% reduction from 2021, but still a substantial and concerning amount. These scams include cryptojacking, where malicious actors hijack a computer’s resources to mine cryptocurrency without the user’s knowledge. Ensuring that your marketing strategy avoids falling victim to such security risks is crucial.
So, the reluctance may be justified. But what can you do as a marketer forced to adapt your crypto marketing strategy in such a way as to bring success to a valid, reliable, and transparent project? Yet, even in the current market situation, with the right crypto marketing strategy, the success of your project can be closer than it looks.
Does this mean you need a major in business and marketing communication? Although any bit of information and training will help you develop your business, a formal major is not mandatory. However, you must design an advanced marketing strategy and pay attention to new trends, platforms, and behaviors the market signals so that your projects grow as expected.
Let’s start from scratch.
Table of Contents
Will a Crypto Marketing Strategy Still Work?
Let’s face it – your crypto marketing strategy cannot be flawless. Not because the strategy is bad but because many factors must be considered.
First, cryptocurrency advertisements are still largely restricted, especially if used for ICO marketing. Although the mainstream ad platforms try to dig into the advertising funds crypto projects have, the regulators have started new initiatives to give out guidelines. And as time passes, these guidelines seem more like crypto ads crackdowns.
Also, we still don’t know if the regulators will just give companies a minor punishment, but it’s a good idea to make changes before you face the consequences.
Second, in 2022 and 2023, cryptocurrency prices had taken a hit. And although the Ethereum merge positive aftermath is still to be seen, the community is also looking forward to the following:
- the US SEC-approved Bitcoin ETF;
- the Solana Mainnet launch;
- the increase in Cardano DeFi Dapps.
Third, communication channels are evolving, and consumer behavior is changing. Not only does the attention span for digital content shorten, but as Nick Morgan, Ph.D., points out, due to the pandemic, people’s ability to engage with new ideas changed as well because of stress and information overload.
There are other factors we didn’t mention here, but to succeed in your crypto marketing effort, you must adapt your approach to the context.
Adapting Your Crypto Digital Marketing
Since 2021, the iOS 14 update has launched continuous hits against digital ad tracking and attribution efficiency.
Modern digital ads are heavily reliant on data to optimize automatically. New privacy regulations like the iOS update and the pending removal of cookies have reduced the data used in artificial intelligence. Furthermore, we found out in January 2022 that Google has laid down the Topics API as a method of tracking users online through a topic-centered tracking system as a part of its plan to phase out cookies in the Chrome web browser.
Also, the EU is once again discussing the ePrivacy Regulation, which is meant to replace Directive 2002/58/EC (Regulation on Privacy and Electronic Communications).
Therefore, meaningful communication and investing in the right channels for the cryptocurrency market have never been more important.
In 2024 and beyond, you should adapt your cryptocurrency digital marketing strategy to make your crypto brand known to relevant communities and engage with the audience in dialogue. As the digital attention span shortens, bite-sized content like short videos, GIFs, and dynamic banners might perform better than traditional ads.
The best way to do that is to explore and invest resources in the platforms that have become more relevant to the crypto community.
Top Platforms You Should Look Into

1. Twitter
It is no secret that many internet users worldwide engage with each other on Twitter to discuss crypto topics. Furthermore, the most relevant figures within cryptocurrency share updates through Twitter.
Also, an earlier study on 682 crypto companies found that 92.8% of cryptocurrency-related projects are active on Twitter.
So, keep your community posted on the state of your operation and upcoming updates, ask questions, and give out answers.
However, don’t go into the monologue trap. Find a network of cryptocurrency pages and engage with them to build a dialogue where new users can join. Use tags and join trending discussions to show your project as a social cryptocurrency brand.
2. TikTok
The general sentiment regarding TikTok is quite mixed. Yet, from a marketing perspective, we need to recognize that this new platform is fulfilling the need for a medium where bite-sized entertaining content rules.
Since its launch in 2016, TikTok has gathered a huge audience of around 1.6 billion monthly active users and 3.5 billion app downloads worldwide. Right now, there aren’t any known restrictions on crypto.
Therefore, as the NFTs market grew, TikTok became quite popular as a marketing channel. Furthermore, TikTok itself has started exploring NFTs as a way to compensate creators.
3. Telegram
Telegram is the most used messaging platform in the cryptocurrency market. In 2024, it had over 950 million active users and was the seventh most downloaded app on iOS and Android.
Therefore, the best practice is to create your own channel and add your team, clients, and other crypto enthusiasts who might be interested in investing in your project.
4. Discord
Discord might not be as popular as Telegram in the crypto market. Yet, its audience has grown to over 140 million, and thanks to its dedicated private server creation capabilities, it continues to be popular in the gaming world.
As gaming, NFTs, and cryptocurrency continue to evolve, the platform becomes increasingly relevant to the crypto market. Therefore, new projects creating complex ecosystems that include NFTs, games, and all kinds of tokens must focus on adding a Discord server to their NFT marketing strategy.
5. Coinzilla
Lastly, an integral crypto marketing strategy must include paid media. But that doesn’t mean launching any digital advertising campaign will get you closer to the desired results.
In addition to the restrictions and requirements mainstream advertising platforms impose, you must consider where your ads are placed. The more contextual they are, the higher their chances of conversion.
Furthermore, static banners are losing more ground every year. Therefore, GIFs and HTML5 banners should be your priority.
In this regard, Coinzilla has built an extensive network of cryptocurrency websites that generate over 1 billion impressions a month from people familiar with the crypto industry. Such a Bitcoin ad network works perfectly for marketing a stake pool or DeFi marketing.
The platform offers a straightforward and efficient campaign dashboard, allowing you to set up ads within minutes. The account managers are also available to assist you and supply you with professionally designed HTML5 banners.
Consider These Factors in Your Crypto Marketing Strategy
Once you’ve settled on the right marketing channels for your crypto project, be careful to set clear goals and expectations for each channel and the outcomes you’re aiming for. To create a successful crypto marketing strategy, keep these essential factors in mind for your channel:
- Be Realistic—Understand that crypto advertising takes time to yield results. The top 20 cryptocurrencies make up the majority of the market. Set achievable goals that match the gradual pace of this ever-evolving market.
- Know Your Audience—It is crucial to have a deep understanding of your target audience. Learn about their likes, preferences, and where they hang out online. Avoid overspending in places where your audience isn’t active. Explore crypto ads and display campaigns on niche websites catering to your specific audience.
- Test the Waters—Try out small-scale test campaigns before diving in completely. These experiments help you gauge the feasibility of your advertising goals and allow you to adjust your approach based on real-world results. It’s all about learning and improving as you go.
Key takeaways
- The crypto advertising sector is receiving more and more legislative attention.
- The cryptocurrency market took a hit in 2022 and 2023, and the Ethereum transition to PoS doesn’t seem to be a turning point.
- Starting with 2022, cookies and privacy are in the spotlight, which might push brands towards more social engagement and niche advertising while using bite-sized entertaining content.
- The best way to adapt your crypto marketing strategy is to explore and invest resources in the platforms that have become more relevant to the crypto community.
- When drafting your crypto marketing strategy, set realistic goals, deeply understand your audience, and test your objectives through small-scale campaigns to refine your approach as you go. Success in crypto marketing is a journey of adaptation and continuous improvement.